SecPoint Penetrator is a powerful vulnerability scanning, assessment & penetration solution that simulates how a hacker or malware could penetrate a given IP and reveal vulnerabilities with reasons and resolution.
Vulnerability Scanning, Assessment, Penetration
![]() Full Privacy – all operations at your defined location
Full Privacy – all operations at your defined location
![]() Advanced AI & Machine Learning
Advanced AI & Machine Learning
![]() Customize reports, branding, Logo
Customize reports, branding, Logo
![]() 11 Vulnerability Scan Profiles & more customizations
11 Vulnerability Scan Profiles & more customizations
![]() WiFi Pen Testing Capability WEP, WPA, WPA2 & WPS
WiFi Pen Testing Capability WEP, WPA, WPA2 & WPS
![]() Training, Setup assistance, User Friendly GUI, Fast Support
Training, Setup assistance, User Friendly GUI, Fast Support
![]() License not locked to IPs. Pay only for concurrent scan size
License not locked to IPs. Pay only for concurrent scan size
Click here for contact or Free Trial information
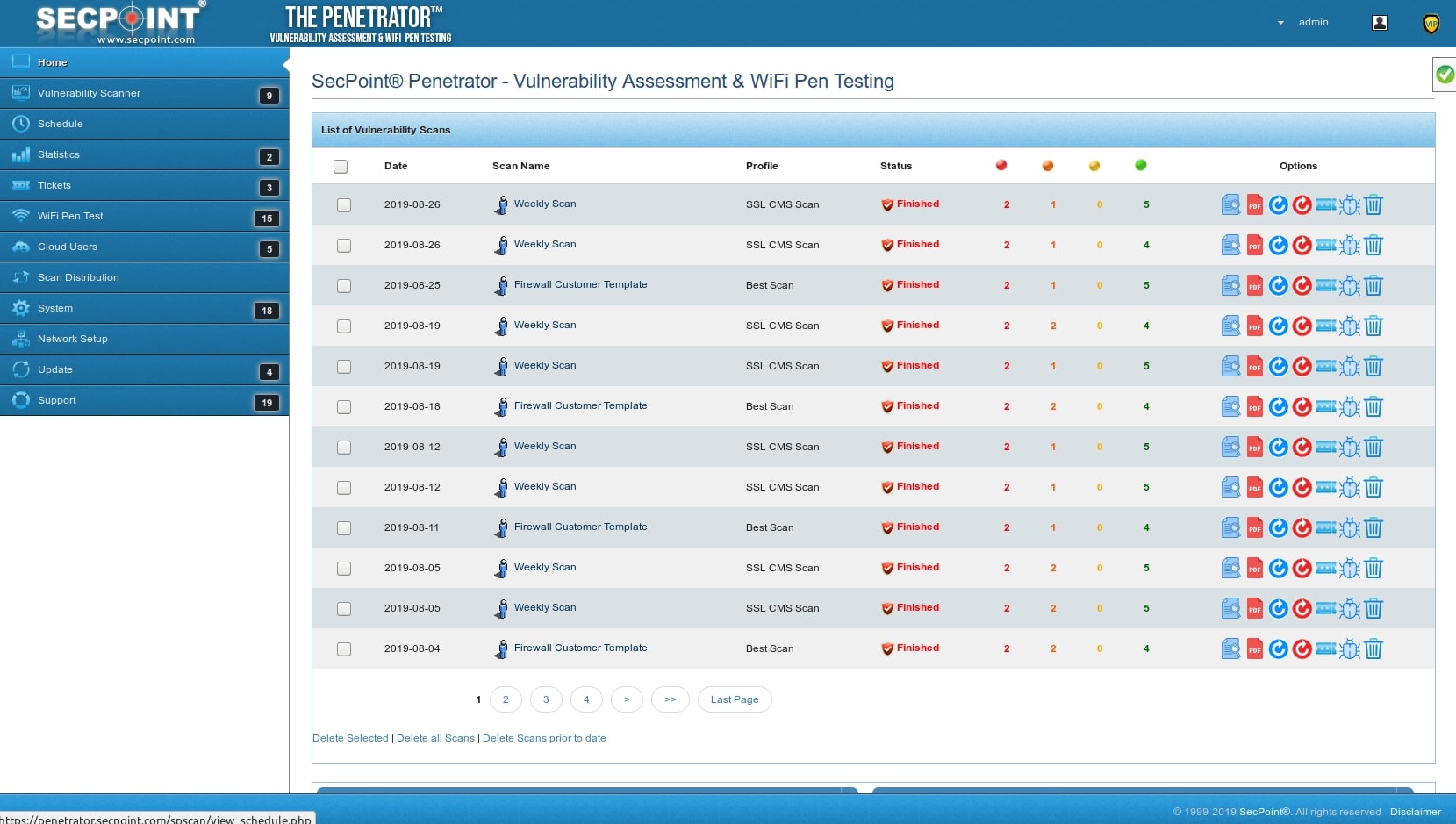
SecPoint Penetrator can help you to find the vulnerabilities on your entire network. You can scan your internal local IP addresses and your public IPs available on the Internet. You can scan your Websites, webapps, servers, workstations, IoT, scada etc. Find all SSL vulnarabilities. SecPoint State of the art Cyber Security and must have for every organization. SecPoint can be installed as harware appliance or virtual machine.
You may find vulnerabilities automatically with the schedule scanning & get notified by email once new vulnerabilities are discovered. PDF & HTML reports will show you the evidence of vulnerabilities and information on how to eliminate them.
SecPoint is fully featured powerful yet easy to use Vulnerability Management – Vulnerability Scanning, Assessment along with real-life pen-testing solution. SecPoint is Number 1 top rated Network Security Vulnerability Scanner, Assessment & Penetration testing solution. Best VAPT – Vulnerability Assessment & Penetration Testing tool.
Features:
- Vulnerability Assessment
- Vulnerability Management
- Launch real exploits
- Penetration Testing
Scanning Features
- Multi User support allows for individual users
- You can scan Local and Public IP addresses. You will get detailed reporting in PDF,HTML or XML.
- It contains clear solutions for the identified vulnerabilities after the vulnerability scanning finished.
- You can easily setup scheduling and get notification once new vulnerabilities gets discovered.
Ransomware Detection
Detect Ransomware throughout the network. Find out if you are vulnerable to popular vulnerabilities exploited by ransomware.
Read more about Ransomware here.
SecPoint Penetrator Important Links
SecPoint Penetrator Brochure – SecPoint Penetrator Datasheet
SecPoint Penetrator Example Output Report
We provide: vapt security, vapt cyber security, vapt services, va pt, vapt assessment, web vapt, vapt, vapt testing, vapt testing online, vapt consultant, network vapt, vapt security testing, web application vapt, vapt meaning, vapt means, vapt scan, meaning of vapt, vapt testing meaning, vapt vulnerability, vapt in cyber security, types of vapt, application vapt, vapt testing full form, cyber security vapt, cloud vapt, vapt full form, vapt reports, vapt companies, vapt certification, vapt testing cost, va and pt, va and pt full form, vapt internship, full form of vapt, vapt solutions, aws vapt, vapt ppt, nessus vapt, va & pt, vapt presentation ppt, mobile vapt, external vapt, vapt certification cost, kali linux vapt, zoom vulnerability, zoom vulnerability 2020, ssl vulnerability scanner, f5 big ip vulnerability, infrastructure pentesting, docker container security scanner, aws vulnerability scanning, open source web application scanner, web server version disclosure vulnerability apache, web server vulnerabilities, vulnerable web application, online web security scanner, cyber security testing services, server vulnerability scanner, server side vulnerabilities, tls 1.3 vulnerability, cloud security scanner, security vulnerability, cve vulnerability, website security scan, remote code execution vulnerability, cloud penetration testing, zoom app vulnerability, security exploit, web app vulnerability scanner, code vulnerability, source code vulnerability scanner, web security vulnerabilities, buffer overflow in cyber security, application vulnerability testing, application security testing services, best penetration testing companies, mobile app vulnerability scanner, web application security vulnerabilities, web services security testing, the metasploit framework, web application penetration testing cost, vulnerability in information security, cloud security testing, cloud security vulnerabilities, tls 1.2 vulnerability, types of security vulnerabilities, zero day attack in cyber security, day zero vulnerability, web application security scanner, web vulnerability scanner, wordpress security scanner, netsparker security scanner, web application vulnerability scanner, security testing application, nessus web application scanning, web security scanner, web application security testing, qualysguard, web server vulnerability scanner, day zero exploit, website security testing, openvas download, application security scanning, manual pen testing, security misconfiguration vulnerability, application vulnerability, cyber security threats and vulnerabilities, site vulnerability scanner, nexpose, free website security scan, security misconfiguration owasp, security testing and penetration testing, open source scan, application vulnerability scan, application vulnerability assessment, app penetration testing, security pen testing, google cloud security scanner, owasp top 10 with examples, zero day exploit attack, open source vulnerability scanner, security testing web, website vulnerability scanner, qualys scan, network security scanner, cyber security and penetration testing, owasp top 10 vulnerabilities 2019, pci vulnerability scan, vulnerability assessment in cyber security, security testing services, pci tests, security and penetration testing, web application vulnerabilities, scan open port, pen testing vendors, black box penetration testing, vulnerability testing and penetration testing, network vulnerability scanner, vulnerability testing software, preventing sql injection, risk assessment and vulnerability analysis, website penetration testing online, penetration testing in cyber security, vulnerability assessment and penetration testing services, owasp top 10 2019, online vulnerability scanner, sql injection vulnerability, open source vulnerability database, database vulnerability scanner, owasp top 10 2017, network security and penetration testing, automated penetration testing, owasp top 10 2020, vulnerability in cyber security, types of vulnerabilities in network security, network security threats and vulnerabilities, types of vulnerability in cyber security, network vulnerability assessment, security vulnerability assessment, web app vulnerabilities, it penetration testing, cve database, online penetration testing, openvas scanner, internal vulnerability assessment, cyber security pen testing, top 10 owasp vulnerabilities 2020, web app scanner, security threats and vulnerabilities, openvas vulnerability scanner, vulnerability database, sql injection example, vulnerability assessment online, penetration testing company, vulnerable websites for testing, vulnerability scanner, owasp top, vulnerability assessment, rapid7 vulnerability scanner, cyber security testing, vulnerability assessment solution, owasp top 10 vulnerabilities 2020, security misconfiguration, server vulnerability assessment, threat vulnerability risk assessment, security vulnerability testing, cloud vulnerability assessment, pen test, national vulnerabilities database, online security testing, use metasploit, server vulnerability, vulnerability penetration testing, owasp vulnerabilities, vulnerability assessment penetration testing, vulnerability analysis and penetration testing, website vulnerability scanner online, vulnerability and penetration testing, vulnerability assessment and penetration testing, cyber security penetration testing, internal penetration testing, vulnerability scanning software, website for penetration testing, web vulnerability scanner online, owasp top 10, owasp top 10 vulnerabilities, openvas, windows vulnerability scanner, pentest, owasp 10, vulnerability analysis, network security penetration testing, owasp mobile top 10, nmap vulnerability scan, web app pentesting, exploit in cyber security, vulnerability assessment companies, web for pentester, day 0 exploit, network security testing, vulnerability in network security, find vulnerabilities in a website, pentest online, web application penetration testing, pen testing, vulnerability testing, application penetration testing, vulnerability in computer security, website vulnerability scanner online free, free vulnerability scanner, online security scanner, nessus pricing, web app penetration testing, vulnerability manager, vulnerability assessment test, container scanning, network penetration testing, website penetration testing, pentest reporting, security testers, nessus professional, free network vulnerability scanner, vulnerability, web application pentesting, free vulnerability scanner online, pen testing companies, nessus vulnerability scanner, tenable nessus, vulnerable websites, web pentesting, risk and vulnerability assessment, software vulnerability, security penetration testing, risk threat vulnerability, pentest website, vulnerability management certification, nessus, nessus scanner, nessus essentials, buffer overflow, external penetration testing, free website vulnerability scanner, online web pentesting, nessus remote security scanner, security scanner, web penetration testing, penetration testing, computer vulnerability, nessus download, network vulnerability, nikto, basic penetration testing, firewall penetration testing, application pen testing, network pentesting, site penetration testing, penetration testing using kali linux, threat vulnerability and risk, cyber penetration testing, owasp top ten, iot vulnerabilities, pentesting companies, server penetration testing, web application vulnerability assessment, system vulnerability assessment, cve testing, kali penetration testing, pentest test, hacking testing, penetration testing with kali linux, cvsss, sql injection, mobile exploit, stagefright, web application scanner, cross site request forgeries, testing pen, authenticated scan, nikto web scanner, shellshock, bluekeep, ripple20, buffer overflow attack, remote code execution, command injection, directory traversal, poodle attack, ldap injection, spectre meltdown, citrix vulnerability, path traversal, code injection, nessus agent, nessus home, cve 2020, php injection, zombieload, arbitrary code execution, cve list, smbghost, zoom vulnerabilities, meltdown spectre, bluekeep vulnerability, cryptoapi, os command injection, directory traversal attack, krack attack, nessus free, spectre and meltdown, injection attack, wordpress vulnerability, sql injection login, bluekeep exploit, wordpress vulnerability scanner, openvas kali, vulnerability examples, sql injection php, meltdown and spectre, f5 vulnerability, wordpress exploit, rce exploit, aws security scanner, rapid7 nexpose, rce vulnerability, shellshock vulnerability, citrix netscaler vulnerability, sql injection attack example, windows 10 vulnerability, microsoft vulnerability, zoom exploit, windows vulnerability, eternal blue exploit, nessus port, nessus pro, intel vulnerability, netscaler vulnerability, nmap script vuln, xss scanner, winbox exploit, nessus login, qualys vmdr, shellshock exploit, windows 10 exploit, ios mail vulnerability, spectre vulnerability, format string vulnerability, tmui, cve security, owasp sql injection, nessus plugins, poodle vulnerability, stack buffer overflow, smb vulnerability, cisco vulnerability, sql injection code, file upload vulnerability, sql injection scanner, cross site scripting vulnerability, nist nvd, drupal 7 exploit, citrix exploit, nist cve, path traversal attack, buffer overflow vulnerability, user enumeration, jquery vulnerabilities, nexpose community edition, nessus manager, smb exploit, path traversal vulnerability, bluekeep metasploit, krack wpa2, buffer overflow attack example, zoom security vulnerability, citrix cve, buffer overflow exploit, nessus kali, nikto kali, wordpress sql injection, zerologon exploit, apache struts vulnerability, apache struts 2, sql injection example login, sql injection code list, nexpose community, bluekeep patch, nessus agent download, qualys vulnerability scanner, rdp vulnerability, php code injection, username enumeration, phpmyadmin exploit, smbv3 vulnerability, php vulnerability, rdp exploit, iis 7.5 exploit, heart bleed, microsoft dns vulnerability, citrix adc vulnerability, website vuln, sql injection online, nvd database, vmdr, kernel exploit, csrf owasp, cisco cdp vulnerability, dns vulnerability, zoom cve, tls 1.1 vulnerability, sql injection commands, qualys free scan, nvd cve, zerologon patch, kali openvas, bluekeep cve, intel meltdown, code execution, drupal exploit, sql injection example url, nexpose rapid7, web vuln, windows 10 vulnerability 2020, microsoft teams vulnerabilities, injection flaws, microsoft teams vulnerability, metasploit linux, owasp scanner, joomla exploit, java deserialization vulnerability, white box penetration testing, nikto scan, spectre intel, php command injection, smbv1 vulnerability, sql injection download, nikto commands, security flaw, microsoft cve, cisco cve, nessus open source, apache vulnerabilities, best web vulnerability scanner, f5 cve, nessus essentials download, eternalblue metasploit, best vulnerability scanner, citrix vulnerability 2020, nessus professional download, nessus kali linux, pentest standard, windows dns vulnerability, tenable nessus download, oracle sql injection, wordpress cve, sql injection kali linux, palo alto vulnerability, ssl poodle, nist vulnerability database, logjam attack, magento exploit, unc path injection, simple sql injection, zoom vulnerability windows, nexus vulnerability scanner, content spoofing, penetration testing framework, mysql sql injection, meltdown vulnerability, greenbone openvas, remote command execution, nikto windows, exploit android, top 10 vulnerabilities, stagefright exploit, windows 7 vulnerabilities, metasploit bluekeep, credentialed scan, command execution, sql injection website, xss script example, ssl vulnerability, tomcat vulnerability, windows 10 vulnerabilities, owasp iot, ripple20 vulnerabilities, nessus docker, wordpress xmlrpc exploit, tomcat exploit, windows cryptoapi spoofing vulnerability, system vulnerability, ios mail app vulnerability, tenable scanner, django sql injection, retina network security scanner, eternal blue cve, owasp iot top 10, wpa2 vulnerability, sql vulnerable sites, nikto download, nessus linux, kali vulnerability scanner, redhat cve, java vulnerabilities, web vulnerability, cyber vulnerability, shellshock attack, sql injection url, exploit code, zoom zero day vulnerability, wpa2 krack, threats and vulnerabilities, ftp vulnerabilities, managed cybersecurity services, cyber threat intelligence platform, computer security company, cyber threat intelligence companies, threat assessment cyber security, cyber security managed services, cybersecurity as a service, cyber security offerings, cyber security threat assessment, multi factor authentication cyber security, companies providing cyber security services, it security assessments, cyber security service offerings, cyber security monitoring services, cyber security assessment services, cyber security service, authentication service security in cyber security, cybersecurity with cloud computing, cyber security solutions, ot cyber security, cyber security services company, cyber intelligence agency, cyber services, scanning in cyber security, cyber security monitoring, cyber security incident management, cyber security assessment, cyber security companies, cyber security aws, vulnerability management in cyber security, google cloud cyber security, cyber security incident response, incident response in cyber security, incident management in cyber security, managed cyber security, security services in cyber security, cyber incident response, threat management in cyber security, cyber security data loss prevention, aws cyber security, cyber security solutions company, cyber security help, cyber security azure, vulnerability scanning in cyber security, scanning cyber security, computer security service, azure cyber security, krack 2017, latest vulnerabilities, sap vulnerability, owasp top ten 2019, teamviewer vulnerability, azure vulnerability assessment, code injection example, intel spectre meltdown, nessus community, jquery cve, critical vulnerability, nessus scanner download, iis 7.5 vulnerabilities, tenable nessus agent, krack vulnerability, nmap vuln, php vulnerability scanner, meltdown intel, sql injection testing, nessus security scanner, docker vulnerability, sql injection string, ajp13 exploit, kali linux openvas, wormable, nessus community edition, code injection attack, vpn vulnerabilities, ldap injection attack, iphone vulnerability, samba exploit, exploit scanner, xss injection example, apache exploit, sql injection list, windows cryptoapi, wordpress exploit scanner, ios exploit, microsoft iis 8.5 vulnerabilities, nmap vuln scan, nessus professional price, cve exploit, tls vulnerability, tomcat cve, heartbleed cve, fortinet vulnerability, remote exploit, nessus free download, nikto online, dns cache poisoning attack, servicenow vulnerability response, teamviewer exploit, cve zoom, xss vulnerabilities, wordpress security vulnerabilities, stored xss example, xss scripting, nessus home download, wordpress user enumeration, php cve, linux vulnerability, intel cpu vulnerability, retina vulnerability scanner, sigred vulnerability, nikto kali linux, wannacry cve, vulnerability list, ios vulnerability, cisco asa vulnerability, port 80 vulnerabilities, apple mail app vulnerability, drupal vulnerability, tenable nessus professional, kali linux vulnerability scanner, nessus windows, python buffer overflow, cross site scripting attack example, nikto example, freak attack, dns exploit, spectre exploit, arbitrary file upload, container vulnerability scanning, php injection example, python code injection, xss code, owasp sensitive data exposure, clickjacking vulnerability, bluekeep scanner, owasp cross site scripting, apache tomcat exploit, apache cve, tenable web application scanning, command injection attack, start nessus, php sql injection example, netscaler cve, cve scanner, sql injection script, apple vulnerability, owasp top 20, external vulnerability scan, struts vulnerability, exploit vulnerability, black penetration, drupal 8 exploit, pentest framework, apache struts exploit, port 443 vulnerabilities, zerologon cve, f5 tmui, container security scanning, smbv1 exploit, nexpose vulnerability scanner, beast vulnerability, cve 2017, vmware vulnerability, bootstrap vulnerabilities, eternal blue vulnerability, network penetration, owasp top ten 2017, windows 7 vulnerabilities 2020, django vulnerabilities, docker security scanning, webex vulnerability, intel zombieload, zero day patch, linux vulnerability scanner, nexpose pricing, sql injection exploit, risk and vulnerability, android cve, security vulnerability examples, wp file manager vulnerability, xss testing, stagefright android, nmap vuln script, sql injection blind, metasploit vulnerability scan, iphone exploit, smbghost exploit, owasp top ten vulnerabilities, coldfusion exploit, coordinated vulnerability disclosure, nessus cloud, penetration testing cost, cve nvd, sharepoint exploit, aws ssrf, microsoft iis 10.0 vulnerabilities, thinkphp remote code execution vulnerability, jquery file upload exploit, teamviewer 7 exploit, nikto website vulnerability scanner, joomla scanner, wordpress xss, f5 exploit, heap overflow attack, xss url, directory traversal vulnerability, docker cve, android vulnerability scanner, xss dom based, citrix netscaler exploit, exploit website, poodle attack ssl, adobe coldfusion 8 exploit, pci penetration testing, qualysguard login, jetty exploit, ripple20 vulnerability, sigred patch, linux kernel exploit, owasp top 10 list, rdp vulnerability 2020, node js vulnerabilities, mysql vulnerabilities, cvssv2, microsoft vulnerability scanner, deserialization vulnerability, rdp patch, smb1 vulnerability, nessus credentialed scan, specter meltdown, linux cve, ssh user enumeration, owasp test, open redirect owasp, exploits web, snmp exploit, drupal 7 vulnerabilities, command injection vulnerability, openvas port, website vulnerability scanner kali, jira exploit, rc4 vulnerability, bluekeep windows 10, xss scanner online, netscaler exploit, openvas greenbone, ms08_067, injection vulnerability, java buffer overflow, dotnetnuke exploit, qualys vulnerability, postfix smtp exploit, database exploit, cve microsoft, exploit windows 10, jenkins vulnerability, jquery exploit, slack vulnerability, nvd vulnerability, best vulnerability scanner 2019, angular vulnerabilities, azure vulnerability scanning, remote os command injection, palo alto cve, apache tomcat vulnerability, web vuln 2020, stored xss attack, snmp vulnerability, smtp vulnerabilities, xmlrpc wordpress exploit, qualys azure, liferay exploit, gitlab container scanning, vuln scanner, intel cpu vulnerability list, bluekeep exploit metasploit, owasp top 10 web, zoom vulnerabilities 2020, sharepoint vulnerability, sigred exploit, logjam vulnerability, litespeed web server exploit, cloud pentesting, configuration compliance scanner, twistlock container scanning, vulnerability attack, risk vulnerability, sql vulnerability, latest cve, draytek vigor remote command execution vulnerability, postfix exploit, metasploit nmap, retina network scanner community edition, openssl cve, types of cross site scripting, black box pentest, kibana exploit, wordpress 5.3 exploit, automated pen testing, xml external entity attack, woocommerce exploit, microsoft windows smbv1 multiple vulnerabilities, zerologon attack, magento vulnerability, sql injection kali, ssrf example, python vulnerabilities, cryptoapi vulnerability, blind sql injection example, sqli attack, tenable nessus scanner, spectre cpu, privilege escalation vulnerability, tenable vulnerability scanner, xss sql injection, sha1 vulnerability, windows vulnerability 2020, tomcat host manager exploit, windows security flaw, vmdr qualys, zoom vulnerability cve, cross site forgery attack, xxe injection example, phpmyadmin vulnerability, remote code execution example, greenbone security, top vulnerabilities, lastpass vulnerability, nikto vulnerability scanner, smbv3 exploit, solarwinds dameware mini remote control unauthenticated rce, php remote code execution, zoom unc vulnerability, user enumeration owasp, nessus cost, bluekeep attack, owasp 2019 top 10, php security vulnerabilities, vulnerability risk assessment, dirty cow vulnerability, tls robot vulnerability, owasp top 10 attacks, owasp vulnerability scanner, bluekeep rdp, xxe attacks, python vulnerability scanner, infrastructure penetration testing, zoom meeting vulnerabilities, cve list 2020, joomla sql injection, angularjs vulnerabilities, website vuln 2020, intrusion testing, owasp top ten 2020, docker exploit, nessus online, iis vulnerabilities, iis 10 vulnerabilities, php 5.6 vulnerabilities, kubernetes cve, nessus penetration testing, php injection attack, rapid7 vulnerability database, wordpress 5.4 exploit, sql injection attack code, netbios vulnerabilities, webmin vulnerability, openvas password, drupal vulnerability scanner, cross site scripting examples, sap recon, xss html, python security vulnerabilities, cyber threat assessment, nexpose scan, memory corruption vulnerability, chrome zero day exploit, wordpress rce, sql injection 2020, metasploit smb exploit, greenbone vulnerability manager, penetration testing standards, zombieload intel, cve 2020 list, manual penetration testing, meltdown and spectre vulnerabilities, cve website, nessus version, penetration testing and ethical hacking, zero day vulnerability list, microsoft iis 7.5 vulnerabilities, docker vulnerability scanner, sigred dns, jquery security vulnerabilities, poodle exploit, metasploit eternalblue, robot vulnerability, threat vulnerability, smb cve, joomla vulnerability scanner, nist vulnerability, smb vulnerabilities, microsoft windows active directory ldap exploit, iis exploit, sql vulnerability scanner, keycloak vulnerabilities, sql injection scanner online, exploit 2020, lucky13 vulnerability, netbios exploit, webmin cve, microsoft zero day vulnerability, owasp open redirect, host header injection owasp, iis 6 exploit, xss vulnerability example, joomla vulnerabilities, google vulnerability, metasploit sql injection, nessus latest version, nginx vulnerability, nodejs vulnerabilities, windows dns server vulnerability, gitlab cve, nmap open port, beyondtrust retina, vulnerability scanning service, nessus audit files, new vulnerabilities, persistent cross site scripting, java deserialization exploit, wannacry vulnerability, jira cve, meltdown exploit, white hat testing, ethical hacking penetration testing, cisco webex vulnerability, overflow attack, security vulnerability database, woocommerce vulnerabilities, azure vulnerability, nessus security, ldap injection example, drupal cve, spectre meltdown patch, big ip vulnerability, privilege elevation, vulnerability response servicenow, nessus scan types, security testing company, nessus vulnerability, cve android, cloud vulnerabilities, fortinet vpn vulnerability, jira vulnerability, microsoft vulnerability 2020, exim vulnerability, weblogic exploit, kubernetes vulnerability, owasp path traversal, buffer overflow code injection example, snyk open source, wordpress vulnerability 2020, directory traversal exploit, nessus free version, cisco ssl vpn exploit, netsparker cloud, command injection examples, spectre and meltdown vulnerabilities, sslv3 vulnerability, tmui f5, citrix vulnerability netscaler, google vulnerability scanner, software vulnerability list, csrf cross site request forgery, port 21 vulnerabilities, cvs vulnerability, hikvision vulnerability, zoom cve 2020, windows 10 cve, clickjacking exploit, eternal blue patch, apple exploit, owasp 2020 top 10, sql injection like, xxe vulnerable application, nessus download for windows 10 64 bit, vulnerabilities examples, red team pentesting, penetration testing pricing, breach vulnerability, intel exploit, wp vulnerability scanner, iphone vulnerability 2020, winbox exploit 2019, teamviewer cve, lucky 13 vulnerability, drupal 8 vulnerabilities, snyk scan, 3389 port exploit, tenable nessus agent download, cyber security assessment and management, java rce, citrix netscaler vulnerabilities, gcp vulnerability scanning, buffer overflow exploit example, ftp anonymous login vulnerability, web directories listable vulnerability, xss example code, ics vulnerabilities, oracle database tns listener poison attack vulnerability, qualys vmdr pricing, confluence exploit, solr exploit, exploit eternalblue, phpunit remote code execution vulnerability, practical web penetration testing, exploit rdp, cisco ios vulnerability, vpn exploit, netscaler vulnerability 2019, crypto vulnerability, nessus features, authentication cyber security, apache tomcat remote code execution vulnerability, eternalblue smb, kubernetes penetration testing, pentest site, proxy server vulnerabilities, smb eternal blue, script xss attack, cve data, xss vulnerable website, dom cross site scripting, confluence cve, port 23 vulnerabilities, vmware vulnerability 2020, zimbra cve, web server scanner, cross scripting attack example, cve file, nessus download kali linux, apache 2.2 vulnerabilities, dirty cow linux, windows zero day vulnerability, ipmi 2.0 rakp authentication remote password hash retrieval vulnerability, rpcbind vulnerability, nessus credentialed scan windows, fortinet vulnerability 2020, cross site scripting javascript, microsoft crypto vulnerability, wordpress 4.6 exploit, azure security center vulnerability assessment, nessus cloud scanner, nessus malware scan, angularjs security vulnerabilities, exploit joomla, remote code injection, top ten owasp 2019, penetration attack, openvas web scanner, cisco jabber vulnerability, citrix adc cve, wordpress vuln, mds attacks, port vulnerabilities list, smb vulnerability 2020, sql injection example code, yoast seo vulnerability, exploit zoom, microsoft ftp service exploit, owasp top 10 web application, bitlocker vulnerability, php file upload vulnerability, magento cve, password reset vulnerability, dns cache poisoning example, haproxy vulnerabilities, nvd security, citrix gateway vulnerability, meltdown cve, pen testing cost, haproxy cve, ios cve, security testing framework, mysql blind sql injection, nasl nessus, apache directory traversal, cisco ripple20, bluekeep rdp exploit, elasticsearch cve, installing nessus, it security penetration testing, ssl renegotiation attack, cisco vulnerability scanner, list of pentesting companies, java serialization vulnerability, sql injection 2019, cve security vulnerability, openvpn vulnerability, liferay cve, nessus key, zoom meeting vulnerability, vulnerability assessment using nmap, zero vulnerability, nessus client, reflected xss attacks, remote code execution exploit, csrf scanner, dejablue vulnerability, openssl exploit, sql injection and cross site scripting, nginx security vulnerabilities, speculative execution vulnerability, wordpress login exploit, spectre cve, arbitrary file upload vulnerability, vbulletin vulnerability, windows rdp exploit, sap cve, top 10 owasp vulnerabilities 2019, speculative execution vulnerabilities, vulnerability assessment azure, confluence vulnerability, f5 k52145254, nessus network scanner, xss cve, azure vulnerability assessment solution, mysql injection attack, ms vulnerability, heartbleed vulnerability exploit, microsoft dns exploit, sql injection 1, tenable nessus login, fortinet ssl vpn vulnerability, home network vulnerability scanner, nessus web port, apache vulnerability scanner, proftpd vulnerabilities, aws vulnerability assessment, elementor pro vulnerability, javascript xss filter, adobe experience manager exploit, stored cross site scripting example, angular cve, cve site, apache security vulnerabilities, dirtycow android, tableau vulnerabilities, smbghost vulnerability, cve whatsapp, xss in url path, apache tomcat 9 vulnerabilities, nessus container scanning, apache struts 2 vulnerability, manual security testing, owasp top 2017, blueborne vulnerability, microsoft rdp vulnerability, wpa2 krack attack, cve redhat, wordpress 0day, database injection attacks, kubernetes exploit, metasploit website, risk and vulnerability analysis, xss input, metasploit cve, the pen test, xss waf, cve sudo, ssl server has sslv3 enabled vulnerability, vulnerability assessment policy, haproxy exploit, nessus ssl certificate cannot be trusted, wordpress directory traversal, smb patch, z xss, google web security scanner, zabbix vulnerabilities, exploit cyber security, samba badlock vulnerability, script injection attack, iframe cross site scripting, web server generic xss, zimbra vulnerability, poodle attack exploit, xss reflected attack, linux 4.15 privilege escalation, slack security vulnerability, windows server 2012 vulnerabilities, wireshark vulnerabilities, 2017 owasp top 10, cyber incident response services, web vulnerability assessment, ms teams vulnerabilities, port 1900 vulnerability, injection attack owasp, php vulnerability scanner online, sql injection cve, sql injection security, directory browsing vulnerability, nmap vulnerability scan command, sql injection wordpress login, windows 10 remote exploits, a zero day vulnerability, microsoft cve list, microsoft internet explorer remote code execution vulnerability, nessus pro price, pci segmentation testing, zecops ios, dns server vulnerability, security misconfiguration attack, citrix vulnerability scanner, oracle weblogic vulnerability, iis 8.0 vulnerabilities, pci vulnerability, intel cpu exploit, owasp 10 2017, f5 big ip cve, type of sql injection, docker scanner, preventing cross site scripting, external scan, kestrel server vulnerabilities, malware exploits, poodle bites vulnerability, remote desktop exploit, modernizr vulnerabilities, buffer overflow code, client potential xss, metasploit shellshock, thinkphp vulnerability, latest vulnerabilities 2020, owasp top 10 xss, shellshock metasploit, websites vulnerable to sql injection, common web application vulnerabilities, unvalidated redirects, scada penetration testing, x frame options header not set vulnerability, smb signing not required vulnerability, ms teams vulnerability, recent vulnerabilities, html sql injection, lfi injection, tls1 0 vulnerability, top 10 vulnerabilities 2020, unrestricted file upload vulnerability, csrf injection, openbsd vulnerabilities, computer penetration testing, port 9000 vulnerabilities, vulnerability assessment scanner, cryptoapi patch, mds intel, penetration testing professional, windows server 2008 r2 vulnerabilities, managed vulnerability scanning, metasploit heartbleed, sap gateway 10kblaze remote code execution vulnerability, xss proxy, nessus pen testing, netscaler patch, internal pentest, diffie hellman vulnerability, veracode penetration testing, website exploit scanner, cisco zero day, nessus debian, blueborne vulnerability scanner, client side vulnerabilities, seven monkeys vulnerability, vmware esxi exploit, pop3 vulnerabilities, spring vulnerabilities, spring cve, start nessus service, best used with vulnerability assessments, md5 vulnerability, openssl heartbleed vulnerability, pentest it, open port 80 vulnerabilities, owasp top 10 web vulnerabilities, qualys network scan, software vulnerability examples, firewall penetration, latest vulnerabilities list, scripting engine memory corruption vulnerability, apache strut, jboss eap 7 exploit, linux kernel vulnerabilities, specter vulnerability, heartbleed security bug, icecast cve, ms dns vulnerability, shellshock linux, scan wordpress site for vulnerabilities, web vulnerability scanner online free, owasp top 10 injection, apache2 exploit, os command injection example, postfix vulnerabilities, self signed certificate vulnerability, windows crypto vulnerability, automated pentesting framework, cbc vulnerability, remote access vulnerabilities, penetration testing best practices, zoom web server vulnerability, citrix application delivery controller and gateway directory traversal vulnerability, heart bleed bug, smb signing not required nessus, dotnetnuke vulnerabilities, ot security assessment, container vulnerability, kernel vulnerability, ms sql injection, overflow vulnerability, owasp top 10 project, security and vulnerability, drupal 7 cve, nginx vulnerabilities 2020, padding oracle on downgraded legacy encryption, csv vulnerability, infrastructure security testing, php file upload exploit, cve day, internet explorer zero day vulnerability, memory corruption exploit, web vuln scanner, wordpress 4.7 exploit, zoom client vulnerability, cyber threat intelligence services, saml vulnerabilities, external vulnerability, database penetration testing, the heartbleed bug, security vulnerability scanning, wordpress vuln scanner, exploit 2019, nessus enterprise, windows 10 security flaws, dirtycow privilege escalation, pci pentest, fortigate vulnerability scan, nessus certificate, stagefright exploit 2020, tenable nessus manager, windows smb remote code execution vulnerability, wordpress plugin exploit, sql injection mariadb, sslv3 poodle vulnerability, owasp top 10 scanner, telnet vulnerability, zeroshell remote command execution vulnerability, google cve, kali linux web vulnerability scanner, linux security scanner, speculative execution attack, tomcat 7 vulnerabilities, bluekeep exploit code, greenbone scanner, new intel vulnerability, servicenow vulnerability, tenable download nessus, wifi krack attack, flash player vulnerabilities, jquery vulnerable versions, tls 1.0 vulnerability list, sql injection vulnerability scanner, cisco patch, latest windows vulnerabilities, hipaa penetration testing, heartbleed metasploit, barco clickshare vulnerability, oracle weblogic exploit, php path traversal, servlet 3.0 vulnerabilities, snmp v2 vulnerabilities, reflected xss owasp, sap netweaver vulnerability, cve in security, docker container scanning, metasploit vulnerability scan commands, preventing xss attacks, qualys web application scanning pricing, java vulnerabilities by version, nessus port 8834, arbitrary file, bluetooth cve, centos 7 vulnerabilities, cryptoapi windows 10, nmap script vulnerability scan, smb null session authentication, wordpress 5.2 exploit, best website vulnerability scanner, path traversal attack example, ssl freak, windows 7 vulnerabilities 2019, owasp top 10 sql injection, zoom waiting room vulnerability, cisco vpn vulnerability, sql injection app, netscaler gateway exploit, microsoft exchange vulnerability, windows server dns vulnerability, apache server vulnerabilities, container vulnerability scanning open source, mariadb vulnerabilities, vbulletin remote code execution vulnerability, professional penetration testing, kibana vulnerabilities, xss python, citrix security bulletins, ios security vulnerabilities, jsof ripple20, jenkins vulnerability scanner, windows smb vulnerability, nessus for windows 10 64 bit, s3 bucket vulnerability, metasploit mikrotik, nessus home edition, remote file inclusion php, tls renegotiation attack, cyber as a service, eternalblue smb exploit, mongodb vulnerability, penetration testing services prices, beast attack tls, ssl poodle vulnerability, common website vulnerabilities, download nessus for kali linux, metasploit server, android app vulnerability scanner, client dom xss, cve online, windows zero day exploit, retina network scanner, xss code injection, zero day vulnerability zoom, apache web server vulnerabilities, fireeye penetration testing, nvd national vulnerability database, pci dss external vulnerability scan, ransomware bluekeep, dns patch microsoft, download winbox exploit, smtp open relay exploit, web sql injection, nmap find vulnerabilities, shell command injection, shellshock code, sql injection username password, citrix adc patch, nist vulnerability scanning, cross site script attack, netscaler security vulnerability, cve fortinet, google chrome vulnerabilities, microsoft netlogon vulnerability, threats attacks and vulnerabilities, vxworks urgent 11, blind based sql injection, xss attack script, nexpose enterprise, redirect vulnerability, ssl tls vulnerabilities, common network vulnerabilities, nessus 8, nessus android, shell upload vulnerability, windows server 2012 r2 vulnerabilities, xss injections, cve python, wpa krack, ssrf scanner, http trace vulnerability, server information disclosure, windows 10 vulnerability scanner, windows server 2003 vulnerabilities, microsoft sigred, pen testing price list, http sql injection, owasp top 10 web application vulnerabilities, sqli login, wireless network penetration testing, xml external entity example, user agent xss, qualys integration, spectre security flaw, sql injection testing website, symantec web gateway remote command execution vulnerability, angular 7 vulnerabilities, jquery vulnerabilities by version, cve database download, cyber exploit, nessus vulnerability scanner download, xss vulnerability scanner, vulnerability monitoring, qualys penetration testing, cdp vulnerability, nexpose community edition download, zoom windows vulnerability, jenkins cve, cpu meltdown, cloud computing threats and vulnerabilities, citrix vulnerability exploit, port 22 vulnerabilities, microsoft dns patch, wordpress plugin vulnerability, file upload exploit, nessus service, heart bleed attack, vmware cve, kubernetes vulnerabilities, openvas online, python cve, nessus server, recent zero day attacks 2019, wordpress vulnerability scanner online, latest vulnerabilities and exploits, snyk vulnerability database, sql injection in cyber security, threat and vulnerability assessment, nmap bluekeep, wordpress vulnerability database, shellshock cve, mysql cve, intel mds, icecast exploit, windows server 2016 exploit, freak vulnerability, cve download, sql injection commands list, cyber vulnerability assessment, nessus download for windows, phpmyadmin sql injection, java cve, poodle tls, threats and vulnerabilities to information security, elasticsearch vulnerability, rce remote code execution, pptp vulnerabilities, wormable vulnerability, cwe xss, cisco asa exploit, php cross site scripting, pci dss penetration testing, url injection attack, exploit xss, citrix netscaler cve, f5 big ip exploit, oracle cve, nessus scanner free, rapid7 scanner, security vulnerability list, sharepoint rce, csrf vulnerabilities, redhat cve database, vulnerable websites list, teamviewer vulnerability 2020, nmap cve scan, openvas login, red team penetration testing, command line vulnerability scanner, fortinet cve, wp vulnerability, windows 10 vulnerabilities 2020, nessus parser, ripple20 exploit, nmap smb vuln scan, microsoft critical patch, internet vulnerability, php code execution, smtp user enumeration, vulnerable websites list 2019, django cve, web penetration, cve login, jira ssrf, citrix vulnerability 2019, nessus reset password, filezilla exploit, linux buffer overflow, cve citrix, software vulnerability database, wpa vulnerability, intel meltdown spectre, security misconfiguration example, owasp vulnerable web application, hsts vulnerability, free web vulnerability scanner, cms vulnerability, gitlab vulnerability, chrome zero day vulnerability, specter and meltdown, vlc vulnerability, rdp bluekeep, snyk vulnerability, aws vulnerability, intel security vulnerability, fortigate ssl vpn vulnerability, nikto linux, nmap vulnerability scan script, risk vulnerability and threat, rabbitmq exploit, flash vulnerabilities, ldap vulnerabilities, nessus cis benchmark, owasp command injection, automated vulnerability scanning, owasp zap sql injection, apache 2.4 vulnerabilities, nessus aws, heartbleed ssl, remote desktop vulnerability, bootstrap exploit, ripple20 cisco, cyber assessment, ssh vulnerability scanner, xmlrpc vulnerability, ckeditor vulnerability, scada vulnerabilities, rapid7 penetration testing, openssh 5.3 vulnerabilities, citrix cve 2019, docker security vulnerabilities, heartbleed openssl, penetration testing service providers, cve cisco, dns vulnerability microsoft, shellshock vulnerability exploit, exchange cve, metasploit attack, grafana vulnerabilities, sslv3 poodle, sql injection time based, threat vulnerability assessment, citrix netscaler patch, rdp cve, saml vulnerability, chrome vulnerabilities, couchdb exploit, grafana cve, intel cve, abyss web server exploit, cyber threat intelligence organizations, postgresql vulnerabilities, typo3 exploit, owasp top 10 vulnerabilities 2017, vulnerability zoom, openssh 7.2 exploit, nessus compiling plugins, latest vulnerabilities and exploits 2019, jetty vulnerabilities, sql injection example login php, ntp mode 6 vulnerability, types of vulnerability scanning, download nessus essentials, bluekeep rdp vulnerability, smb cve 2017, uncredentialed vulnerability scan, cve patch, cpu vulnerability, command injection commands, nessus port scan, cisco exploit, kali web vulnerability scanner, winrar exploit, fortigate exploit, session fixation owasp, check penetration testing, external pen test, metasploit 5, windows server vulnerability, wordpress sql injection example, penetration testing for dummies, white box pen testing, cve20200601, bluekeep vulnerability patch, latest vulnerabilities and exploits 2020, file upload vulnerability exploit, drupal rce, llmnr vulnerability, chrome 0day, sack panic, nessus plugin download, nginx exploits, port 3389 vulnerability, top 10 security vulnerabilities, open source network vulnerability scanner, stagefright android 2019, meltdown cpu, metasploit web, xss javascript example, cyber security assurance, types of vulnerabilities in information security, zombie poodle vulnerability, sql injection login page, mds vulnerability, active directory vulnerabilities, remote code execution in web application, liferay vulnerabilities, passive vulnerability scanner, iot vulnerability scanner, imagemagick vulnerability, it vulnerability, snyk container scanning, struts exploit, windows server 2016 vulnerabilities, windows dns patch, nessus corrupt database, wireless vulnerabilities, wordpress 5.3 vulnerabilities, application security vulnerabilities, windows dns server remote code execution vulnerability, windows server 2012 r2 exploit, tp link vulnerability, flash exploit, open source security scanner, cms exploit, cve code, weak password vulnerability, external vulnerability assessment, network penetration testing services, tomcat vulnerability 2020, script vuln nmap, iot security vulnerabilities, port 443 exploit, xss online, cve windows 10, elevation of privilege attack, apache tomcat ajp file inclusion vulnerability, winrar vulnerability, credentialed vulnerability scan, 5 penetration, nist vulnerability assessment, apk vulnerability scanner, persistent xss attack, cve format, open source web vulnerability scanner, filezilla vulnerabilities, owasp 10 vulnerabilities, open source vulnerability, jquery ui vulnerabilities, nessus openvas, cyber protection services, centos vulnerabilities, php buffer overflow, nexpose free, xss file upload, server side request forgery example, cyber incident management, session fixation vulnerability, broken access control vulnerability, tcp vulnerability, nvd vulnerability database, command execution vulnerability, it vulnerability assessment, java jmx server insecure configuration remote code execution vulnerability, cross site forgery request, nessus cve, pci dss scan, php directory traversal, cve common vulnerability, traversal attack, cbc cipher vulnerability, joomla cve, secura zerologon, crypt32 vulnerability, tenable cve, rdp vulnerability 2019, vulnerability response, cyber threats and vulnerabilities, mobile device vulnerabilities, timthumb exploit, netscaler vulnerability 2020, top 10 vulnerabilities 2019, webex vulnerability 2020, citrix netscaler vulnerability 2020, it exploits the dns system, nessus compliance scan, nessus windows 10 64 bit, tenable vulnerability, nessus essentials login, routeros exploit, ip vulnerability scanner, nessus command line, reflected xss vulnerability, zero day flaw, 3389 exploit, weblogic vulnerability, remote buffer overflow, sharepoint cve, pci network vulnerability scan, jquery xss vulnerability, ssl weak cipher suite selection vulnerability, internal vulnerability scanner, windows zerologon, best vulnerability scanner 2020, cve cyber, dom xss scanner, qualys security scan, cve 20201472, apa itu penetration testing, microsoft zero day patch, google chrome zero day vulnerability, metasploit exploit list, wannacry exploit, java security vulnerabilities, angular security vulnerabilities, cryptoapi spoofing vulnerability, recent sql injection attacks, teamviewer version 7 exploit, tenable nessus pro, windows bluekeep, exploit the dns system, metasploit 2020, http trace exploit, intel processor vulnerability, big ip exploit, stored xss vulnerability, etag header exploit, zero day security, zero logon vulnerability microsoft, openvas on kali, exploit upload shell, nessus web client, vsftpd vulnerabilities, vulnerability assessment e penetration test, ssl exploit, system penetration testing, heap overflow exploit, openvas linux, php remote file inclusion, linux exploits, nessus manager download, cisco vulnerability 2020, cve bluekeep, citrix gateway exploit, owasp top 10 2019 list, sigred microsoft, recent buffer overflow attacks, cve cybersecurity, iphone zero day, url redirection vulnerability, intel vulnerability 2019, non persistent xss, file path traversal, owasp directory traversal, apache solr exploit, f5 big ip vulnerabilities, zero click exploit, smbv3 patch, nessus professional cost, windows security vulnerability, xpath injection attack, cve jquery, new cve, wordpress 5.4 vulnerabilities, windows rdp vulnerability, zerologon kb, eternalblue scanner, cloud web security scanner, user enumeration vulnerability, top 10 web vulnerabilities, cdp vulnerability cisco, smb wannacry, nessus download windows 10 64 bit, nmap open port scan, microsoft exploit, palo alto exploit, libssh exploit, sap recon vulnerability, xss website, beast ssl, computer security and penetration testing, plugin vulnerabilities, zerologin vulnerability, internet of things vulnerabilities, microsoft crypto patch, jetty cve, nessus metasploit, latest owasp top 10, nessus authenticated scan, cloud vulnerability scanning, cve wannacry, phpinfo vulnerability, cisco asa cve, jboss vulnerability, reflective cross site scripting, struts2 exploit, coordinated disclosure, crime vulnerability, cve example, tenable forrester, blind sql injection exploit, drupal sql injection, iso 27001 penetration testing, remote code execution attack, dhcp vulnerabilities, sftp vulnerabilities, wireshark vulnerability scanner, beast attack ssl, fortigate vulnerability, poodle attack cve, snyk container, stack buffer overrun, git cve, hikvision vulnerability 2019, internal network penetration testing, metasploit scan host for vulnerabilities, stack buffer overflow attack, cross origin resource sharing vulnerability, java exploit, penetration testing vendors, mvpower dvr tv shell unauthenticated command execution vulnerability, tls protocol session renegotiation security vulnerability, sql injection sql server, nessus url, sql injection php login, ssl 3.0 vulnerability, webdav vulnerability, rapid7 nexpose pricing, rdp exploit 2020, code execution vulnerability, ubuntu 18.04 vulnerabilities, owa exploit, return of bleichenbacher’s oracle threat, best free vulnerability scanner, csrf wordpress, microsoft security flaw, msf metasploit, external entity injection, apache shellshock, sudo vulnerability 2019, cve software, aws cve, jira vulnerabilities, cve docker, dompurify xss, openvas version, simple xss, windows server 2008 vulnerabilities, common web vulnerabilities, apache struts cve, sap exploit, aws ec2 vulnerability scanning, krack exploit, xss jquery, ghost cat vulnerability, mssql exploit, nessus download kali, tcp timestamp vulnerability, weblogic rce, xss php example, microsoft smb vulnerability, tp link exploit, aws ecr vulnerability scanning, known vulnerabilities database, http host header attack, php 5.6 exploit, rdp bluekeep vulnerability, system penetration, windows server 2003 exploit, citrix cve 2020, 2nd order sql injection, nis cybersecurity, web vuln sql, continuous penetration testing, wordpress 5.0 exploit, digital forensics incident response, drupal core remote code execution vulnerability, stack overflow vulnerability, hikvision exploit 2019, nessus free download for windows 10 64 bit, recent sql injection attacks 2019, cyber intelligence services, active vulnerability scan, adobe flash vulnerabilities, patch vulnerability, bluekeep patch windows 7, ntlm vulnerabilities, ipv6 vulnerabilities, network vulnerability tests, symantec vulnerability, penetration testing firms, vpn vulnerabilities 2020, http response header injection, iis 6.0 vulnerabilities, openvas free, mac os vulnerabilities, cloud vulnerability management, meltdown patch, blind sql injection attack, microsoft security vulnerability, penetration testing consulting services, saas cyber security, reporting security vulnerabilities, web server vulnerability, website security vulnerabilities, online web application scanner, online website security scanner, vulnerability detection, website security scanner, best web application vulnerability scanner, free web security scanner, free website security scanner, application vulnerability scanner, top penetration testing companies, network security companies, pci vulnerability scanning, cyber network security, zero day cyber security vulnerability, ransomware vulnerability, it security companies, web app vulnerability, iot penetration testing, network and cyber security, online website scanner for vulnerabilities, vulnerability testing online, penetration testing api, computer network and cyber security, cyber security risks threats and vulnerabilities, website vulnerability testing, network security and cyber security, free web application scanner, wireless penetration testing, cyber security firewall, latest zero day vulnerability, find vulnerabilities in a website online, vulnerability scanning with nmap, network security services company, security testing for beginners, vulnerability assessment certification, wifi penetration testing, personal cyber security services, managing vulnerabilities, cyber security it companies, web vulnerability testing, certified penetration tester, vapt software, certified pen tester, penetration testing beginners, app security scanner, va scanning, xss, xss example, xss vulnerability, xss injection, types of vulnerability, sql injection types, physical penetration testing, basic sql injection, types of xss, example of vulnerability, google xss, persistent xss, xss exploit, router exploit, xss in url, sql injection command, wep vulnerabilities, xss vulnerable websites, javascript for pentesters, xss security, windows vulnerabilities, router vulnerability, types of exploits, netgear vulnerability, wifi vulnerability, physical security penetration testing, wps vulnerability, netgear router vulnerability, physical pentesting, sql injection detection, basic pentesting, physical penetration, javascript vulnerability scanner, intel chip vulnerability, sql code injection, denial of service vulnerability, intel cpu security flaw, wireless pentesting, latest security vulnerabilities, windows penetration testing, firewall vulnerability, intruder vulnerability scanner, new exploit, wifi penetration, exploit server, ddos vulnerability, in band sql injection, physical pen testers, example of cross site scripting, sql injection hacking, joomla security scanner, webcruiser web vulnerability scanner, wlan vulnerabilities, xss code example, javascript security scanner, physical security testing, admin sql injection, sql injection html, google penetration testing, penetration testing proposal, ptes pentest, gcp cloud security scanner, pentest website online, external vulnerability scanner, router penetration testing, cyber testing, security penetration, vulnerability wordpress, types of software vulnerabilities, wireless network vulnerabilities, xss exploit example, kali website vulnerability scanner, sqli vulnerability, jquery cross site scripting, penetration testing platform, sql injection example site, nessus vulnerability assessment, web server penetration testing, ptes penetration testing, xss and sql injection, xss vulnerability in wordpress, external network penetration testing, sql injection code for login, vuln sql injection, it security vulnerability, vulnerability assessment plan, va vulnerability assessment, web application penetration, cybersecurity vulnerability assessment, pentest pricing, web services penetration testing, java vulnerability scanner, vulnerability testing services, sql server vulnerabilities, reflected cross site scripting example, risk vulnerability & threat in a network, exploit in computer security, web app security scanner, site scripting, cross site scripting stored, xss in javascript, false positive vulnerability, cloud penetration, intel chip security flaw, port vulnerability, web application vulnerability testing, wifi vulnerability scanner, wordpress cross site scripting, application security penetration testing, joomla exploit scanner, app vulnerability scanner, port vulnerability scanner, windows null session, cpu spectre, penetration scan, software security vulnerabilities, types of vulnerabilities in cyber security, white hat pen testing, passive vulnerability scanning, security vulnerability analysis, types of sqli, known exploits, cross site scripting java, cross site scripting testing, cyber security threat management, different types of sql injection, cyber threat prevention, cms vulnerability scanner, pentest firewall, xss url example, a xss, intel cpu vulnerabilities, xss cross site scripting example, becoming a pen tester, sql vulnerability scanner online, free online sql injection scanner, online vuln scanner, threat and vulnerability risk assessment, cloud based vulnerability scanner, vulnerability scanning and penetration testing, pentest automation, remote penetration testing, crowdsourced penetration testing, jquery cross site scripting vulnerability, google redirect exploit, sharepoint penetration testing, best network vulnerability scanner, firewall vulnerability assessment, pentesting box, secureworks penetration testing, sql injection is, network penetration testing and ethical hacking, top pentesting companies, free online pentest, free pentest online, network vulnerability analysis, pen test results, sql injection risk, internal and external penetration testing, cross site scripting code, firewall threats and vulnerabilities, security vulnerabilities of a proxy server, sql injection cross site scripting, operating system vulnerability, website penetration, different types of system vulnerabilities, pentesting for dummies, penetration testing security analysis, find vulnerabilities, find xss vulnerability, php penetration testing, ano ang vulnerability assessment, database vulnerability assessment, cyber security management services, pentest sql injection, security testing and ethical hacking, website vuln scanner, intel processor security flaw, pentest server, gartner vulnerability assessment, zero days cyber security, attack and penetration testing, cross scripting example, free sql injection scanner, google cloud web security scanner, penetration testing providers, vulnerabilities and exploits, blind penetration testing, owasp security scanner, s xss, vulnerability web, network security vulnerability assessment, vulnerability in it, mass sql injection, web server exploits, web vuln scanner online, types of network vulnerabilities, hacking vulnerabilities, easy sql injection, internet security scanner, sharepoint vulnerability scanner, best xss scanner, owasp pen testing, pci dss vulnerability scanning, windows server vulnerability scanner, sql injection and, host based vulnerability scanner, best web application scanner, cyber vulnerability management, cpu vulnerabilities, spectre meltdown intel, computer exploits, firewall vulnerability scanner, misconfiguration vulnerability, pentest scan, zero day hacking, host vulnerability scanner, domain vulnerability scanner, spectre cpu vulnerability, top website vulnerabilities, blind cross site scripting, google zero day vulnerability, os vulnerability scanner, physical security vulnerability assessment, wifi security testing, qualys vulnerability assessment, vulnerability to information security, xss url injection, physical vulnerability assessment, xss vulnerable site, sql injection penetration testing, acunetix penetration testing, css cross site scripting, online vulnerability, vulnerability in hacking, xss testing site, cloud security penetration testing, use of sql injection, cross scripting vulnerability, network exploits, nessus web scanner, router vulnerability scanner, ai penetration testing, ec council penetration testing, find sql injection, identifying vulnerabilities, missing http security headers vulnerability, penetration testing strategy, sqli scanner online, xss database, becoming a penetration tester, penetration testing fundamentals, security threat risk assessment, url vulnerability scanner, exploit in information security, pentest black box white box, server security misconfiguration, js vulnerability scanner, penetration test results, cyber security vulnerability management, pen testing firms, cross site scripting ppt, pentest cyber security, ai pentesting, xss testing website, infrastructure vulnerability management, pc vulnerability scanner, app vulnerabilities, auto sql injection, microsoft penetration testing, pen testing services cost, best penetration testing, waf cross site scripting, data penetration, xss scripting example, network infrastructure vulnerabilities, vulnerability code, current vulnerabilities, most common security vulnerabilities, security penetration testing companies, threat and vulnerability analysis, cross site vulnerability, joomla vulnerability scanner online, recent vulnerability, vulnerabilities cyber security, xss to sql injection, chrome cross site scripting, google cloud vulnerability scanning, javascript pentesting, http cross site scripting vulnerability, agent based vulnerability scanner, owasp web scanner, sql injection pentest, missing security headers vulnerability, xss in cyber security, recent security vulnerabilities, saas vulnerability scanner, security exploits list, sql injection flaws, website vulnerability assessment, inurl sql injection, owasp vulnerability assessment, vulnerability assessment and management, exploit testing, penetration testing team, new zero day vulnerability, sql injection and its types, cyber security and management, cross site scripting example javascript, database sql injection, rc4 cipher vulnerability, social engineering vulnerabilities, threats and vulnerabilities in information security, web application penetration testing service, ethical penetration testing, sql penetration testing, va pentest, firewall pentesting, penetration testing and vulnerability scanning, site vulnerability assessment, wireless penetration, cross site scripting w3schools, intel processor security vulnerability, network vulnerabilities list, web vulnerability list, most common web security vulnerabilities, site pentest, penetration testing in ethical hacking, black box penetration, website security penetration testing, internal vulnerability, cross site scripting iframe, cyber security testing company, home vulnerability scanner, owasp online scanner, best pentest companies, dynamic vulnerability scanning, data penetration testing, persistence penetration testing, website for sql injection testing, example of vulnerability in computer security, sql injection firewall, sql injection threat, intel meltdown patch, automatic sql injection, intel security bug, vulnerability zero day, information security penetration testing, penetration testing attacks, penetration testing operating systems, vulnerability risk and threat, web server misconfiguration, cross site scripting exploit, security threat and risk assessment, exploit xss vulnerability, pentest platform, intel cpu vulnerability 2020, saas penetration testing, common web security vulnerabilities, in xss, managed security systems, sql injection vulnerability example, vulnerable risk assessment, top 10 vulnerability scanner, vuln site, internal penetration, day 0 vulnerability, intel cpu meltdown, zero day vulnerability 2020, sql injection website example, wordpress security scanner online, automating vulnerability assessments, intel security vulnerabilities, vulnerabilities of information systems, wpa exploit, xss through url, free windows vulnerability scanner, xss csrf sql injection, wpa3 vulnerabilities, penetration testing business, system misconfiguration, vlc media player vulnerabilities, xss cross scripting, cross site scripting vulnerability example, artificial intelligence vulnerabilities, enterprise vulnerability scanner, php exploit scanner, ceh penetration testing, online owasp scanner, web application security penetration testing, cross site scripting in php, free owasp scanner, latest threats and vulnerabilities, check pen testing, possible sql injection, cyber security vulnerability list, pentesting hacking, assets threats and vulnerabilities, basic sql injection example, vulnerability in risk management, white hacker and pen tester, context pen testing, cross site scripting example code, network vulnerabilities and threats, best sql injection, vulnerability spectre, ot penetration testing, database pentesting, known security vulnerabilities, latest exploit, internet vulnerability scanner, manual penetration, online site vulnerability scanner, learning sql injection, about sql injection, penetration t, vulnerability and risk management, computer network vulnerabilities, latest zero day vulnerability 2019, router pentesting, security threats and vulnerability, cross site scripting header, html cross site scripting, most common network security vulnerabilities, different types of vulnerabilities in cyber security, network vulnerability monitoring, php code vulnerability scanner online, asset threat vulnerability, best test pen, cyber security testing companies, best free vulnerability scanner 2020, google cross site scripting, online sqli scanner, cross site scripting scanner, javascript vulnerability scanner online, computer penetration, cyber and penetration tests for web applications, sql vulnerable website, vulnerability assessment uk, javascript penetration testing, penetration testing solutions, proxy vulnerabilities, vulnerability control, xss scanner online free, diffie hellman vulnerabilities, sql injection application, kali linux find vulnerabilities, vulnerability management risks, system vulnerability scanning, intel new vulnerability, tenable vulnerability assessment, spectre meltdown cpu, sql injection in login, xss flaw, different types of vulnerabilities, penetration assessment, pentesting web services, cyber penetration, free web application vulnerability scanner, sql injection true, sql injection user password, cross site scripting injection, identifying security vulnerabilities, website for pentesting, it threats and vulnerabilities, vulnerability assessment cost, annual penetration test, best security scanner, cyber security exploits, vlc vulnerabilities, free xss vulnerability scanner, intel spectre and meltdown, pentest online scan, pentesting app, vulnerability scanner download, reflected cross site scripting vulnerability, remote pentesting, penetration and vulnerability tester, spectre processor, computer vulnerability scanner, cross site scripting chrome, cybersecurity and threat management, pentest ip, cross site scripting security, perform penetration testing, sql injection types owasp, threat exploit vulnerability, vulnerability cyber, manual pentesting, vulnerability tracking software, gray box vulnerability testing, cross site scripting kali linux, find sql injection vulnerability, firewall security testing, free network security scanner, vulnerability scanning system, cpu meltdown spectre, cyber security protection services, penetration testing companies near me, pentesting and vulnerability assessment, sqli vulnerability scanner, cybersecurity saas companies, exploit in network security, inferential sql injection, continuous pentesting, intel cpu flaws, self cross site scripting, site vulnerable sql 2020, nessus online vulnerability scanner, software vulnerability in information security, vulnerability scanning ppt, website scanner for javascript vulnerabilities and security headers, famous security vulnerabilities, owasp website scanner, known vulnerability, vulnerability scan metasploit, vulnerable software list, windows for pentesting, acas vulnerability scanner, network threats and vulnerabilities, vulnerability assessment pricing, sql injection login password, host vulnerability, penetration testing assessment, penetration testing audit, practical web application penetration testing, scada vulnerabilities list, top vulnerability scanner, independent penetration testing, firmware vulnerability scanner, vulnerability management cyber security, assessment cyber security, continuous vulnerability assessment, data security penetration testing, vulnweb sql injection, best web vulnerability scanner online, different vulnerabilities, pentest proposal, sql injection in sql, ad penetration testing, apa itu web vuln, dhs vulnerability assessment, gaining access penetration testing, xss html example, cpu security flaws, exploit scanner online, javascript for xss, owasp scanner online, security and vulnerability testing, types of vulnerability in computer security, core penetration testing, sql injection website login, web based vulnerability scanner, mitigating sql injection, sqli vuln online shop, use of penetration testing, meltdown cpu vulnerability, zero day exploit chrome, penetration testing project, generic sql injection, vulnerable to security threats, cyber security assessment companies, inurl xss, xss example website, zero day database, internal network vulnerability scanner, monitoring cyber security, computer system vulnerabilities, security services in computer security, vulnerability analysis in ethical hacking, vulnerability in web application, vulnerability scanning service pricing, zero day exploits list, csrf scanner online, types of cyber security vulnerabilities, cgi sql injection, iso penetration testing, pen test box, penetration testing weidman, cyber security s, ip penetration testing, vulnerability assessment management, black box testing in cyber security, kali test website for vulnerabilities, vulnerability scanner free online, pentesting on windows, spectre intel bug, types of vulnerability in security, application security testing companies, most popular vulnerabilities, vlc player vulnerability, iis cross site scripting, vulnerability evaluation, cyber security services for companies, pentest results, sql injection web application, web security sql injection, java penetration testing, personal security in cyber security, sql injection password example, bug exploits, cyber security personal, smtp relay vulnerability, types of cyber vulnerabilities, wireless security testing, best pentesting companies, external vulnerability scanning service, vulnerability analysis plan, managed vulnerability assessment, penetration box, praetorian penetration testing, remote vulnerability scanner, xml cross site scripting, free wordpress vulnerability scanner, it penetration, online network vulnerability scanner, risk of sql injection, different types of cross site scripting, pentest infrastructure, sql injection for windows, xss scanner free, best website security scanner, microsoft exchange vulnerabilities, scada system vulnerabilities, vulnerability software scanner, pentest xss, understanding sql injection, web pentest online, best free web vulnerability scanner, black box vulnerability testing, internet vulnerability assessment, penetration testing environment, penetration testing windows 10, simple penetration testing, vulnerability scanner nmap, apa itu vulnerability assessment, pentest findings, potential sql injection, security and vulnerability assessment, computer security penetration testing, vulnerability web application, black hat pen testing, cross site scripting url example, intel cpu spectre, network penetration testing cost, probably security scanner, windows 10 penetration testing, wordpress exploit scanner online, common cybersecurity vulnerabilities, cross site scripting in javascript, exploit website vulnerabilities, sql injection vulnerable code, hipaa vulnerability management, threats risks and vulnerabilities, cross site hacking, http vulnerability scanner, penetration testing and vulnerability analysis, pentest vulnerability assessment, embedded systems vulnerabilities, penetration testing website online, site vulnerable sql, vulnerability survey, infosec penetration testing, intel cpu security vulnerabilities, ip vulnerability scanner online free, local vulnerability scanner, networking for pentesters, penetration testing consulting, pos vulnerabilities, spectre vulnerabilities, wireless lan vulnerabilities, processor vulnerabilities, web server security scanner, login with sql injection, online sql injection vulnerability scanner, pentest audit, wordpress xss scanner, best vulnerability scanner kali linux, openvas vulnerability assessment, pentest vulnerability scanner, zero day exploit website, database security scanner, most common sql injection, stuxnet zero day vulnerabilities, zero day ddos, external penetration testing cost, passive penetration testing, penetration test e vulnerability assessment, website for vulnerability testing, xss vulnerable code example, false vulnerability, free xss scanner, php website vulnerability scanner, server security scanner, sql injection bug, sql injection on login, cross site scripting html, cyber security zero day, intitle penetration testing, proxy server security vulnerabilities, saas cyber security companies, vulnerability in cyber security ppt, vulnerability injection, website with sql injection vulnerability, wlan software vulnerabilities, 0 exploit, application of penetration test, automated web vulnerability scanner, owasp top 10 cross site scripting, pentesting cloud services, top penetration testing firms, vulnerability scanning management, business vulnerability assessment, data security vulnerabilities, google cloud vulnerability scanner, rf penetration testing, ddi vulnerability scanning, infrastructure vulnerability scanning, system security vulnerabilities, information system vulnerabilities, intel meltdown vulnerability, ips sql injection, sans vulnerability assessment, vulnerability assessment in cloud computing, threat vulnerability and risk assessment, web security scanner google, cpu vulnerability spectre, free vulnerability scanner for windows, it security vulnerability assessment, web application penetration testing companies, potential xss vulnerability, superveda sql injection, web based vulnerabilities, black box web application penetration testing, ip address vulnerability scanner, nessus web vulnerability scanner, penetration testing compliance, penetration testing near me, vulnerabilities of web applications, cgi vulnerability scanner, http security vulnerabilities, ai vulnerability scanner, automated vulnerability detection, cyber security network monitoring, cybersecurity professional penetration tester, endpoint vulnerability scanner, free web app vulnerability scanner, joomla xss, xss sql injection example, asp vulnerability scanner, ip vulnerability scanner online, most popular vulnerability scanner, vulnerability in system security, agent based vulnerability scanning, cross site scripting php example, cyber security sql injection, example of threat and vulnerability, penetration testing on website, scada security testing, machine learning vulnerability scanning, public ip vulnerability scanner, xss from url, free php vulnerability scanner, gray box pentest, top security vulnerabilities 2019, conducting vulnerability assessments, penetration testing 2020, router threats and vulnerabilities, server security testing, vulnerability app, web server pentesting, automated vulnerability testing, black box and white box penetration testing, get based sql injection, penetration testing on windows, scanning in penetration testing, building vulnerability assessment, exploitation penetration testing, identifying security threats, pentest web server, vulnerability scanning types, automated security scanning, easy penetration testing, penetration testing risk assessment, new security vulnerability, simple cross site scripting example, types of security vulnerability, web exploit scanner,